Glory Info About What Is The Purpose Of Point-to-point

Unveiling the "Why" Behind Point-to-Point Connections
1. Why Bother with Point-to-Point?
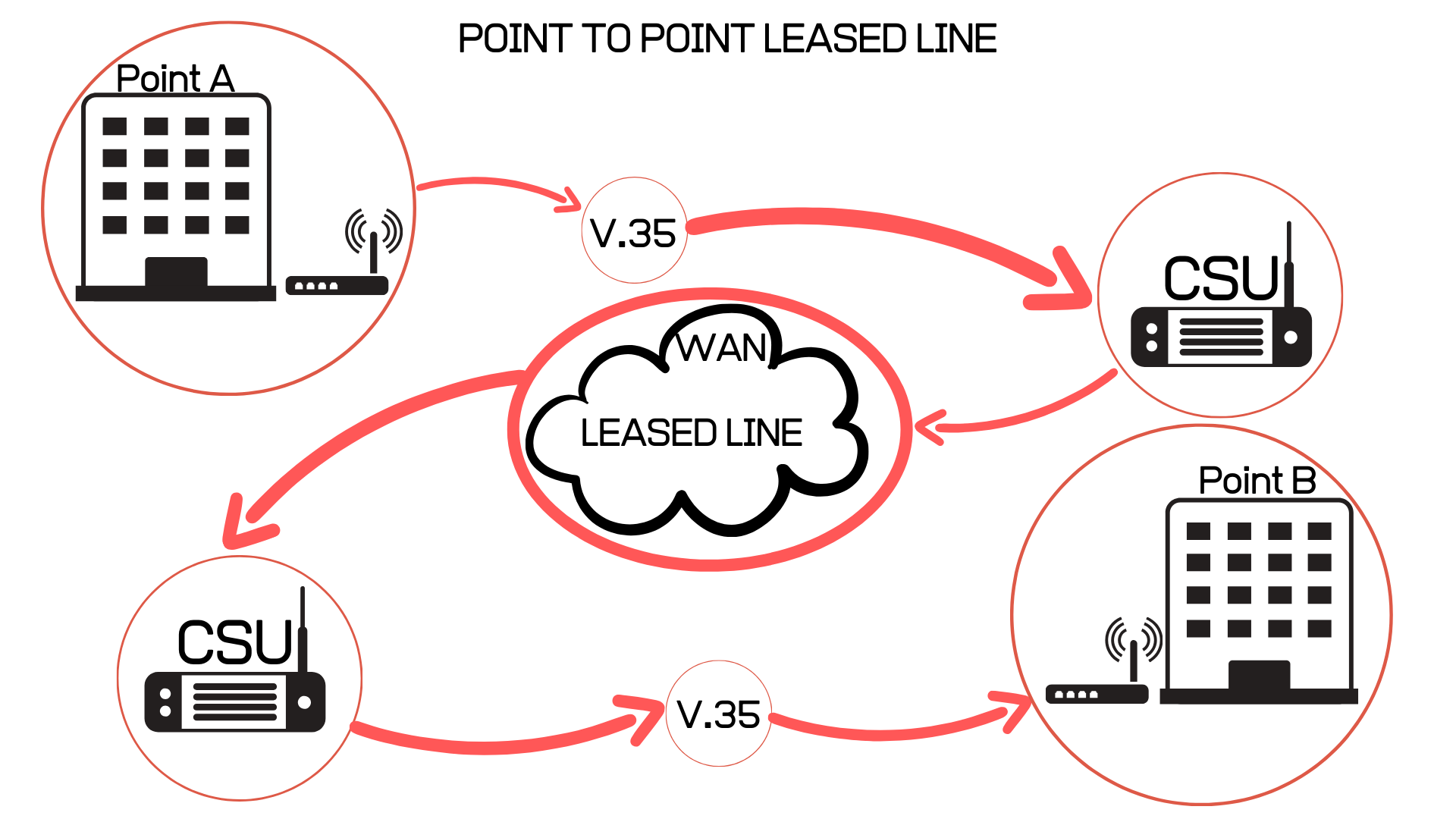
Ever feel like you're shouting into the void online? In the world of data and networking, a point-to-point connection is the opposite of that feeling. It's like having a private phone line straight to your best friend — only instead of gossip, it's data zipping back and forth. The primary purpose, in the simplest terms, is to establish a dedicated, direct communication pathway between two specific locations. No noisy neighbors, no crowded hallways, just a straight shot.
Think of it like this: imagine you need to send a sensitive document from your office in New York to a branch office in London. You could send it through the regular internet, where it might bounce through multiple servers and potentially be intercepted. Or, you could set up a point-to-point connection. This creates a secure, reliable tunnel just for your data, cutting out the middlemen and reducing the risk of eavesdropping. Its all about control and security when sharing what's essential.
But it's not just about security, though thats a huge part. It's also about predictability. With a direct link, you know exactly what kind of bandwidth youre getting and can often guarantee a certain level of performance. This is critical for applications where every millisecond counts, like real-time data streaming or financial transactions. It's the difference between getting a blurry Zoom call that cuts out every two seconds and smooth, consistent communication.
So, the fundamental purpose of point-to-point connections revolves around establishing secure, reliable, and predictable communication links between precisely two points. It eliminates the uncertainties and potential vulnerabilities that come with shared networks. Businesses and organizations often choose point-to-point links when dealing with sensitive data, demanding real-time applications, or require stringent control over their network performance.

Md5 To Decrypt TechFest Hub
Diving Deeper
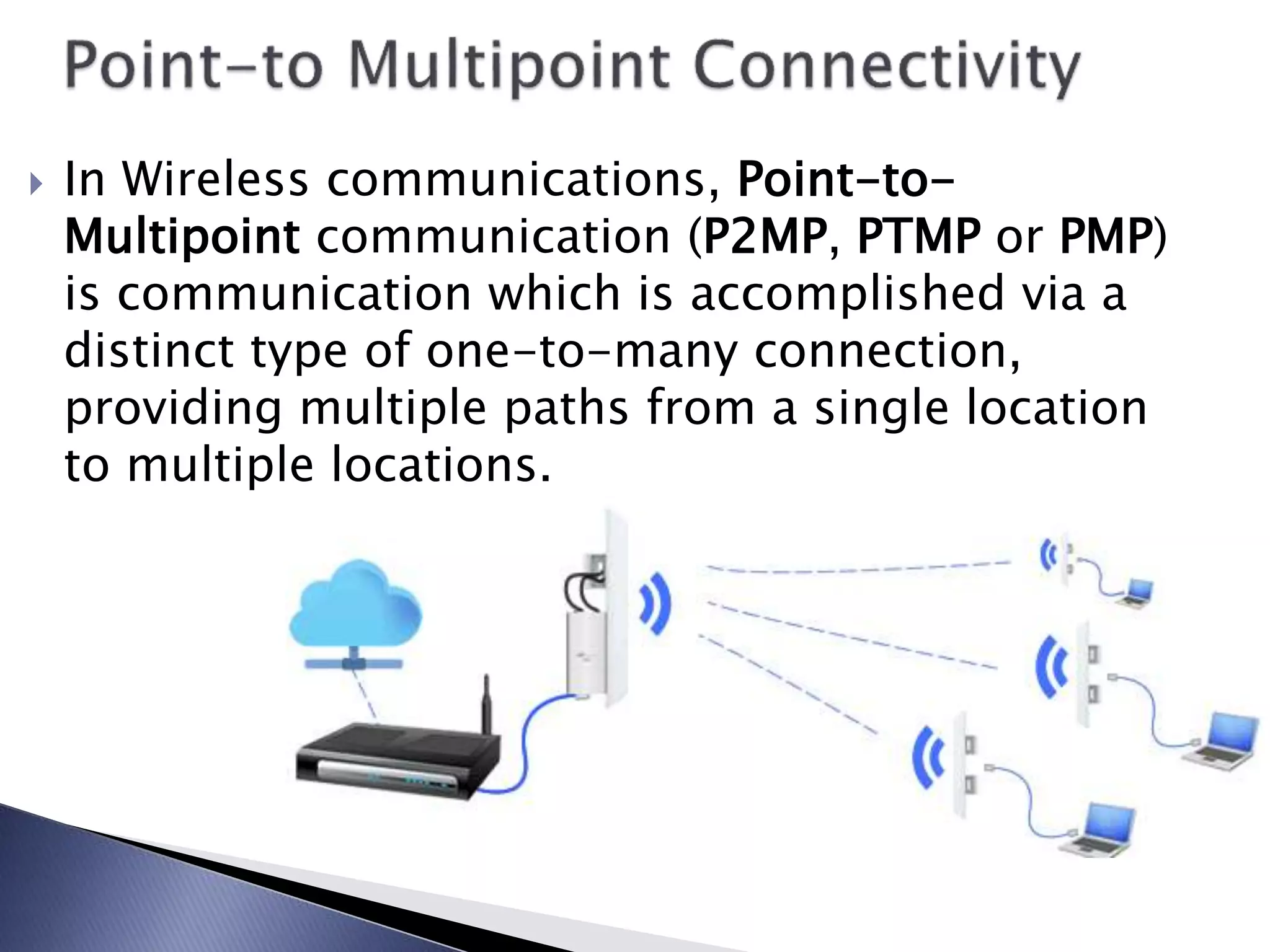
2. Where Does Point-to-Point Shine?
Okay, so we know it's a dedicated link. But where does point-to-point really excel? Well, a lot of big businesses rely on them to keep their data moving securely and efficiently between offices. Think of multinational corporations connecting headquarters to regional hubs — it's like having their own private internet.
Beyond the corporate world, scientific research benefits hugely from this technology. Imagine a telescope in Chile beaming astronomical data back to a university lab in California. A dedicated connection ensures those precious observations arrive quickly and without errors, allowing researchers to make groundbreaking discoveries sooner.
Even the financial industry relies heavily on point-to-point connections. High-frequency trading firms, for example, need the fastest possible links to stock exchanges to execute trades in milliseconds. A delay of even a tiny fraction of a second could mean the difference between profit and loss, so reliability and speed are paramount. That's where point-to-point networks truly come into their own.
Telecommunications providers, too, use point-to-point links extensively. They form the backbone of many long-distance phone and internet services. These connections allow service providers to deliver consistent bandwidth and reliable connectivity to end-users, even across vast distances. It's a foundation of the global communication system.
Purpose Statement All You Need To Know SM Insight
Security Considerations
3. Locking Down the Data Highway
One of the most appealing aspects of point-to-point connections is their inherent security advantages. Because the link is dedicated, there's far less risk of interception compared to data traveling across a public network. Think of it as a tunnel with only two entrances, making it infinitely harder for someone to sneak in unnoticed.
However, don't think that a dedicated link automatically equals impenetrable security. While the risk of eavesdropping is reduced, it's still crucial to implement strong encryption protocols to protect the data being transmitted. This is especially important when dealing with highly sensitive information, such as financial records or personal data. It's about layers of defense.
Physical security is also an essential consideration. Protecting the physical infrastructure that supports the point-to-point connection is vital. This could involve securing access to network equipment, implementing surveillance systems, and conducting regular security audits. Remember, a chain is only as strong as its weakest link, and physical vulnerabilities can easily compromise the entire system.
Regularly updating security protocols and conducting vulnerability assessments are also important. As technology evolves, so do the tactics of cybercriminals. Staying one step ahead requires constant vigilance and a proactive approach to security. It's about identifying and addressing potential weaknesses before they can be exploited, ensuring that your point-to-point connection remains a secure and trusted pathway for your valuable data.
Point Topoint And Pointto Multipoint Wireless Connectivity PPT
Performance and Reliability
4. Making Sure Things Run Smoothly
Beyond security, performance and reliability are huge factors driving the use of point-to-point connections. With a dedicated link, you get predictable bandwidth and low latency, which is crucial for real-time applications. Imagine trying to play a fast-paced online game with a laggy connection; it's frustrating! Point-to-point networks help eliminate that frustration.
Reliability also translates to minimal downtime. When businesses depend on constant connectivity, any disruption can be costly. Point-to-point connections are designed with redundancy in mind, often using backup systems to ensure that data flow continues even if one component fails. Its a bit like having a spare tire for your car — you hope you never need it, but youre grateful when you do.
Monitoring performance is also vital. Regularly tracking bandwidth utilization, latency, and error rates helps identify potential problems before they impact operations. This proactive approach allows network administrators to optimize performance and prevent disruptions. Its like getting a regular checkup at the doctor to catch any health issues early on.
Effective Quality of Service (QoS) mechanisms also play a crucial role in maintaining performance and reliability. By prioritizing different types of traffic, QoS ensures that critical applications receive the bandwidth they need, even during periods of high network utilization. It's about making sure that the most important data gets through first, keeping business-critical operations running smoothly and without interruption.
Cost Considerations
5. The Price Tag of Exclusivity
Let's be honest: point-to-point connections typically come with a higher price tag compared to shared network solutions. The dedicated infrastructure and specialized equipment required can represent a significant upfront investment. It's like buying a custom-made suit versus one off the rack — you're paying for exclusivity and tailoring.
However, it's crucial to weigh the costs against the benefits. Consider the potential cost of a security breach or a network outage. The financial losses, reputational damage, and disruption to business operations can far outweigh the initial investment in a secure and reliable point-to-point connection. It's a calculation of risk versus reward.
Furthermore, the cost of bandwidth is not always the only factor. Consider operational costs, such as the staffing needed to manage and maintain the network. While point-to-point connections require skilled IT professionals, the increased reliability and reduced downtime can ultimately lead to lower operational costs in the long run. It's about looking at the total cost of ownership over the lifespan of the connection.
The overall value proposition of point-to-point connections lies in their ability to provide a secure, reliable, and high-performance communication link that minimizes risk and maximizes efficiency. While the initial investment may be higher, the long-term benefits can often outweigh the costs, making it a worthwhile investment for organizations that prioritize security, reliability, and control over their network infrastructure.
Point To Networks The Best Guide Leased Line Comparison
FAQ
6. Your Burning Questions Answered
Got more questions? You're not alone! Here are some common queries about point-to-point connections:
Q: Is point-to-point always the most secure option?A: While inherently more secure than shared networks due to its dedicated nature, point-to-point still requires robust encryption and physical security measures to protect against potential vulnerabilities. It's a strong foundation, but needs reinforcement.
Q: Can I use point-to-point for home internet?A: Technically, yes, but it's generally overkill and far too expensive for typical home use. Point-to-point is usually reserved for businesses and organizations with specific security and performance needs. Think of it as using a Formula 1 race car to drive to the grocery store possible, but impractical.
Q: What are some alternatives to point-to-point connections?A: Depending on your needs, options include Virtual Private Networks (VPNs), Multiprotocol Label Switching (MPLS), and secure cloud-based solutions. Each has its own advantages and disadvantages in terms of cost, security, and performance, so it's important to carefully evaluate your requirements before making a decision. It depends on the task at hand which solution will do the best job.